LLTP ransomware removal instructions
LLTP ransomware removal instructions
What is LLTP?
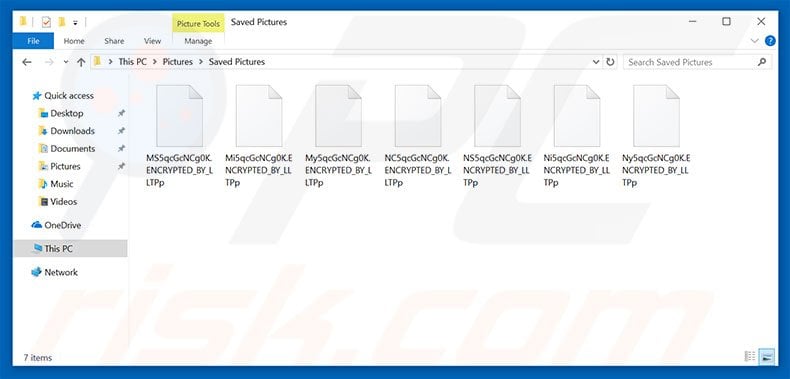
First discovered by malware researcher, MalwareHunterTeam, LLTP is an updated version of a ransomware-type virus called VenusLocker. Once infiltrated, LLTP encrypts files using AES-256 and RSA-2048 algorithms. In addition, the virus renames encrypted files by encoding the original filenames with Base64 scheme. It also changes the file extension to either ".ENCRYPTED_BY_LLTP" or ".ENCRYPTED_BY_LLTPp" (depending on the type of file). For example, "1.jpg" might be renamed to "MS5qcGcNCg0K.ENCRYPTED_BY_LLTPp". After successfully encrypting files, LLTP changes the desktop wallpaper, opens a pop-up window, and creates a text file ("LEAME.txt"), placing it on the desktop. All three contain ransom demand messages.
Note that the LLTP messages within the wallpaper, text file, and pop-up are not identical. The wallpaper and text file contain messages in English, whilst the pop-up's is in Spanish. Delivering different messages in this fashion is quite uncommon to ransomware-type viruses. Although the languages are different, they deliver an identical message: files are encrypted and the victim must purchase a unique key to restore them. As mentioned above, LLTP uses AES-256 and RSA-2048 cryptographies. Therefore, restoring files without unique keys is impossible. To receive these keys, victims must send the equivalent of $200 in Bitcoins to cyber criminals. Research shows, however, that criminals often ignore victims, once payments are submitted. Thus, paying does not guarantee that your files will ever be decrypted and there is a high probability that you will be scammed. You are strongly advised to ignore all requests to pay or contact these people. Unfortunately, there are no tools capable of decrypting files compromised by LLTP ransomware. The only solution is to restore files/system from a backup.
Screenshot of a message encouraging users to pay a ransom to decrypt their compromised data:
There are many ransomware-type viruses virtually identical to LLTP. The list of examples includes CryptoDevil, ZinoCrypt, RozaLocker, and Enjey Crypter. Note that, as with LLTP, these viruses also encrypt files and make ransom demands. There are just two major differences: 1) cost of decryption, and; 2) type of encryption algorithm [symmetric/asymmetric] used. Even the distribution methods are identical. Ransomware-type viruses are often distributed via spam emails (infectious attachments), peer-to-peer networks (torrents, etc.), third party software download sources (freeware download websites, free file hosting websites, etc.), fake software update tools, and trojans. Therefore, be very cautious when opening files received from suspicious emails, and when downloading software from unofficial sources. Furthermore, keep your installed applications up-to-date and use a legitimate anti-virus/anti-spyware suite. Bear in mind, however, that criminals often employ fake updaters to proliferate malware. Therefore never update software via third party tools. The key to computer safety is caution.
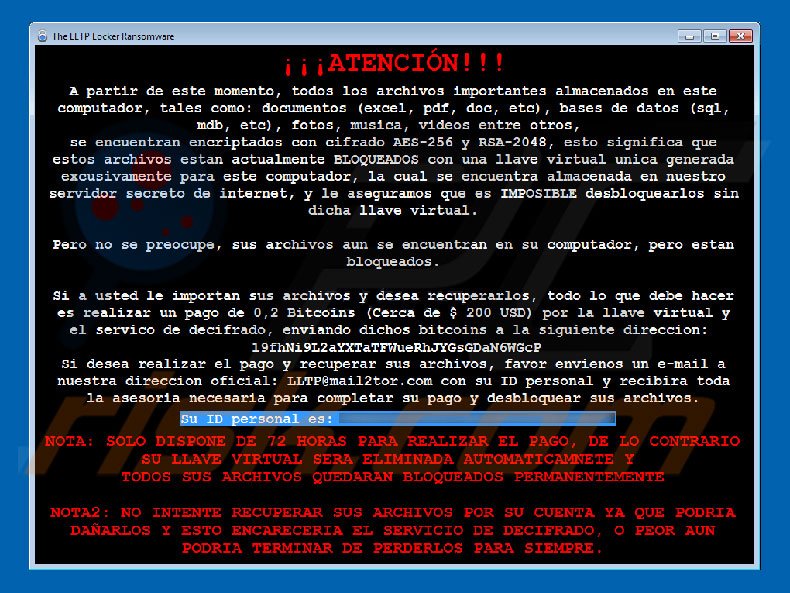
Ransom-demand message presented within LLTP ransomware pop-up:
A partir de este momento, todos los archivos importantes almacenados en este computador, tales como: documentos (excel, pdf, doc, etc), bases de datos (sql, mdb, etc), fotos, musica, videos entre otros,
se encuentran encriptados con cifrado AES-256 y RSA-2048, esto significa que estos archivos estan actualmente BLOQUEADOS con una llave virtual unica generada excusivamente para este computador, la cual se encuentra almacenada en nuestro servidor secreto de internet, y le aseguramos que es IMPOSIBLE desbloquearlos sin dicha llave virtual.
Pero no se preocupe, sus archivos aun se encuentran en su computador, pero estan bloqueados.
Si a usted le importan sus archivos y desea recuperarlos, todo lo que debe hacer es realizar un pago de 0,2 Bitcoins (Cerca de $ 200 USD) por la llave virtual y el servico de decifrado, enviando dichos bitcoins a la siguiente direccion:
Si desea realizar el pago y recuperar sus archivos, favor envienos un e-mail a nuestra direccion oficial: LLTP@mail2tor.com con su ID personal y recibira toda la asesoria necesaria para completar su pago y desbloquear sus archivos.
NOTA: SOLO DISPONE DE 72 HORAS PARA REALIZAR EL PAGO, DE LO CONTRARIO SU LLAVE VIRTUAL SERA ELIMINADA AUTOMATICAMNETE Y
TODOS SUS ARCHIVOS QUEDARAN BLOQUEADOS PERMANENTEMENTE
NOTA2: NO INTENTE RECUPERAR SUS ARCHIVOS POR SU CUENTA YA QUE PODRIA DAÑARLOS Y ESTO ENCARECERIA EL SERVICIO DE DECIFRADO, O PEOR AUN PODRIA TERMINAR DE PERDERLOS PARA SIEMPRE.
Screenshot of LLTP ransomware text file ("LEAME.txt"):
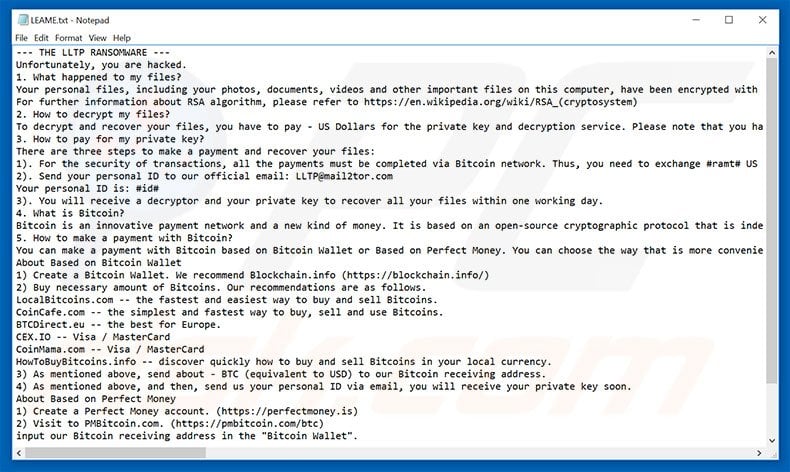
Text presented within LLTP ransomware text file:
--- THE LLTP RANSOMWARE ---
Unfortunately, you are hacked.
1. What happened to my files?
Your personal files, including your photos, documents, videos and other important files on this computer, have been encrypted with RSA-4096, the strongest encryption algorithm. RSA algorithm generates a public key and a private key for your computer. The public key was used to encrypt your files a moment ago. The private key is necessary for you to decrypt and recover your files. Now, your private key is stored on our secret Internet server. And there is no doubt that no one can recover your files without your private key.
For further information about RSA algorithm, please refer to hxxps://en.wikipedia.org/wiki/RSA_(cryptosystem)
2. How to decrypt my files?
To decrypt and recover your files, you have to pay - US Dollars for the private key and decryption service. Please note that you have ONLY 72 HOURS to complete your payment. If your payment do not be completed within time limit, your private key will be deleted automatically by our server. All your files will be permanently encrypted and nobody can recover them. Therefore, it is advised that you'd better not waste your time, because there is no other way to recover your files except making a payment.
3. How to pay for my private key?
There are three steps to make a payment and recover your files:
1). For the security of transactions, all the payments must be completed via Bitcoin network. Thus, you need to exchange #ramt# US dollars (or equivalent local currencies) to Bitcoins, and then send these Bitcoins (about BTC) to the following address. 19fhNi9L2aYXTaTFWueRhJYGsGDaN6WGcP
2). Send your personal ID to our official email: LLTP@mail2tor.com
Your personal ID is: -
3). You will receive a decryptor and your private key to recover all your files within one working day.
4. What is Bitcoin?
Bitcoin is an innovative payment network and a new kind of money. It is based on an open-source cryptographic protocol that is independent of any central authority. Bitcoins can be transferred through a computer or a smartphone with an intermediate financial institution.
5. How to make a payment with Bitcoin?
You can make a payment with Bitcoin based on Bitcoin Wallet or Based on Perfect Money. You can choose the way that is more convenient for you.
About Based on Bitcoin Wallet
1) Create a Bitcoin Wallet. We recommend Blockchain.info (hxxps://blockchain.info/)
2) Buy necessary amount of Bitcoins. Our recommendations are as follows.
LocalBitcoins.com -- the fastest and easiest way to buy and sell Bitcoins.
CoinCafe.com -- the simplest and fastest way to buy, sell and use Bitcoins.
BTCDirect.eu -- the best for Europe.
CEX.IO -- Visa / MasterCard
CoinMama.com -- Visa / MasterCard
HowToBuyBitcoins.info -- discover quickly how to buy and sell Bitcoins in your local currency.
3) As mentioned above, send about - BTC (equivalent to USD) to our Bitcoin receiving address.
4) As mentioned above, and then, send us your personal ID via email, you will receive your private key soon.
About Based on Perfect Money
1) Create a Perfect Money account. (hxxps://perfectmoney.is)
2) Visit to PMBitcoin.com. (hxxps://pmbitcoin.com/btc)
input our Bitcoin receiving address in the "Bitcoin Wallet".
input - in the "Amount", the amount of Bitcoin will be calculated automatically.
click "PAY" button, then you can complete you payment with your Perfect Money account and local debit card.
6. If you have any problem, please feel free to contact us via official email.
Best Regards
The LLTP Locker Team
Screenshot of LLTP desktop wallpaper:
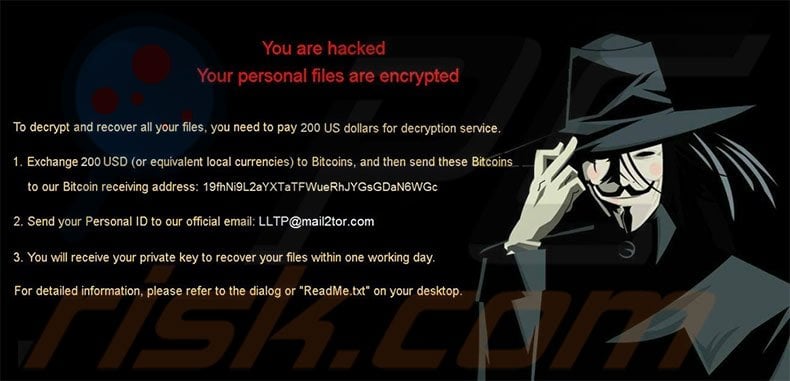
Text file presented within LLTP ransomware desktop wallpaper:
You are hacked
Your personal files are encrypted
To decrypt and recover all your files, you need to pay 200 US dollars for decryption service.
1. Exchange 200 USD (or equivalent local currencies) to Bitcoins, and then send these Bitcoins to our Bitcoin receiving address: 19fhNi9L2aYXTaTFWueRhJYGsGDaN6WGc
2. Send your Personal ID to our official email: LLTP@mail2tor.com
3 You will receive your private key to recover your files within on working day.
For detailed information, please refer to the dialog or “ReadMe.txt” on your desktop.
Screenshot of files encrypted by LLTP (Base64 encoded filename with ".ENCRYPTED_BY_LLTP" or ".ENCRYPTED_BY_LLTPp" extension):
LLTP ransomware removal:
- What is LLTP?
- STEP 1. LLTP virus removal using safe mode with networking.
- STEP 2. LLTP ransomware removal using System Restore.
Step 1
Windows XP and Windows 7 users: Start your computer in Safe Mode. Click Start, click Shut Down, click Restart, click OK. During your computer start process, press the F8 key on your keyboard multiple times until you see the Windows Advanced Option menu, and then select Safe Mode with Networking from the list.
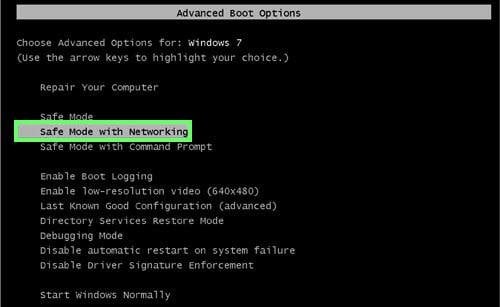
Video showing how to start Windows 7 in "Safe Mode with Networking":
Windows 8 users: Start Windows 8 is Safe Mode with Networking - Go to Windows 8 Start Screen, type Advanced, in the search results select Settings. Click Advanced startup options, in the opened "General PC Settings" window, select Advanced startup. Click the "Restart now" button. Your computer will now restart into the "Advanced Startup options menu". Click the "Troubleshoot" button, and then click the "Advanced options" button. In the advanced option screen, click "Startup settings". Click the "Restart" button. Your PC will restart into the Startup Settings screen. Press F5 to boot in Safe Mode with Networking.
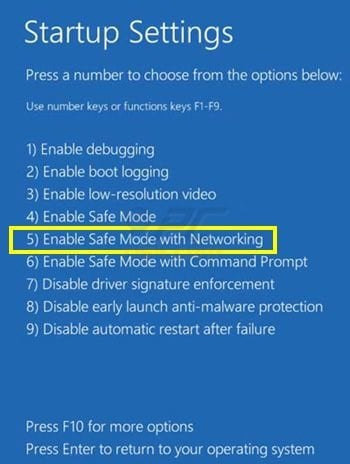
Video showing how to start Windows 8 in "Safe Mode with Networking":
Windows 10 users: Click the Windows logo and select the Power icon. In the opened menu click "Restart" while holding "Shift" button on your keyboard. In the "choose an option" window click on the "Troubleshoot", next select "Advanced options". In the advanced options menu select "Startup Settings" and click on the "Restart" button. In the following window you should click the "F5" button on your keyboard. This will restart your operating system in safe mode with networking.
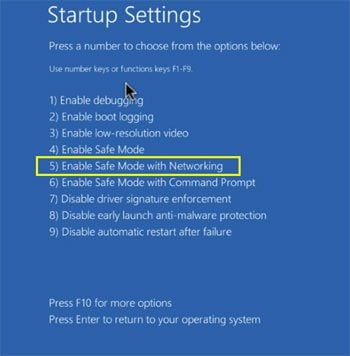
Video showing how to start Windows 10 in "Safe Mode with Networking":
Step 2
Log in to the account infected with the LLTP virus. Start your Internet browser and download a legitimate anti-spyware program. Update the anti-spyware software and start a full system scan. Remove all entries detected.
If you need assistance removing lltp , give us a call 24/7:
1-866-208-0865
1-866-208-0865
By downloading any software listed on this website you agree to our Privacy Policy and Terms of Use. SpyHunter’s free scanner is for malware detection. To remove the detected infections you will need to purchase a full version of this product. More information on SpyHunter. If you wish to uninstall SpyHunter follow these instructions. All the products we recommend were carefully tested and approved by our technicians as being one of the most effective solutions for removing this threat.
If you cannot start your computer in Safe Mode with Networking, try performing a System Restore.
Video showing how to remove ransomware virus using "Safe Mode with Command Prompt" and "System Restore":
1. During your computer start process, press the F8 key on your keyboard multiple times until the Windows Advanced Options menu appears, and then select Safe Mode with Command Prompt from the list and press ENTER.
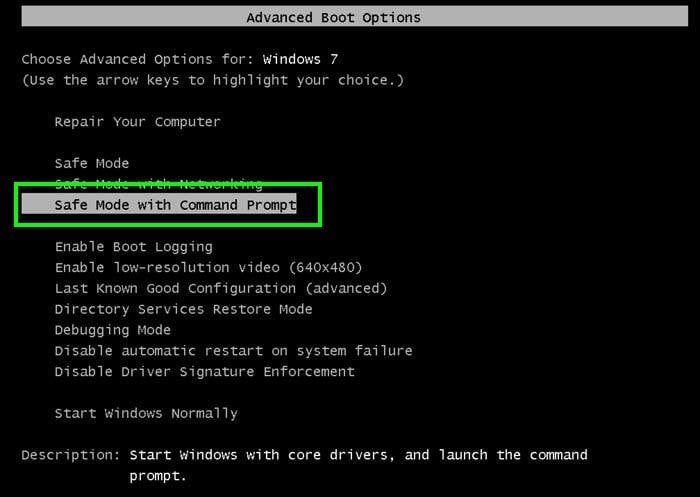
2. When Command Prompt mode loads, enter the following line: cd restore and press ENTER.
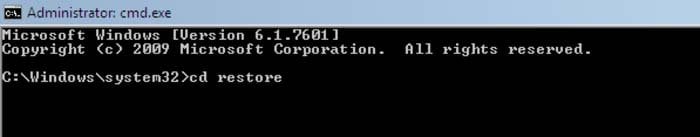
3. Next, type this line: rstrui.exe and press ENTER.
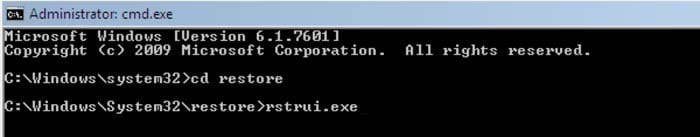
4. In the opened window, click "Next".
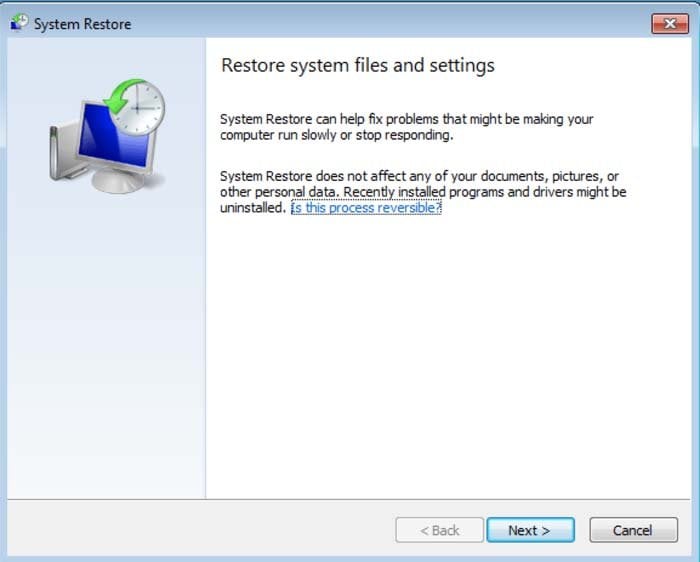
5. Select one of the available Restore Points and click "Next" (this will restore your computer system to an earlier time and date, prior to the LLTP ransomware virus infiltrating your PC).
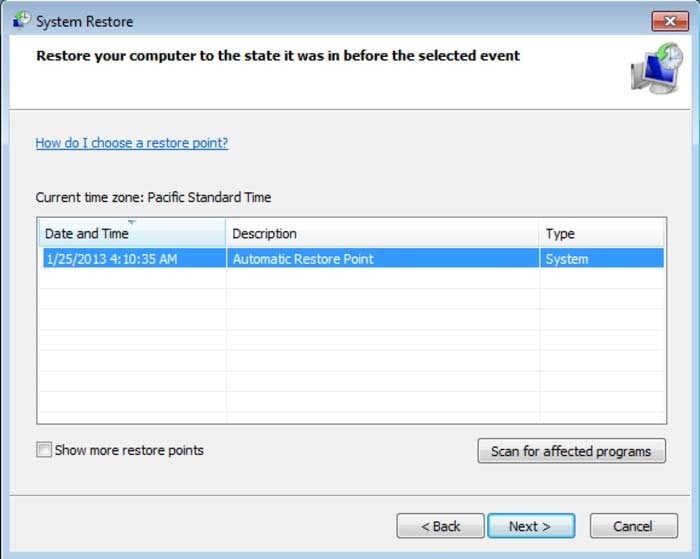
6. In the opened window, click "Yes".
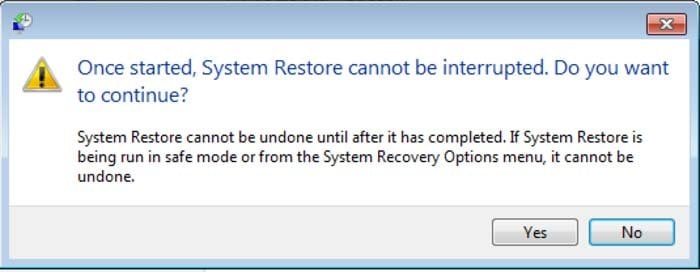
7. After restoring your computer to a previous date, download and scan your PC with recommended malware removal software to eliminate any remaining LLTP ransomware files.
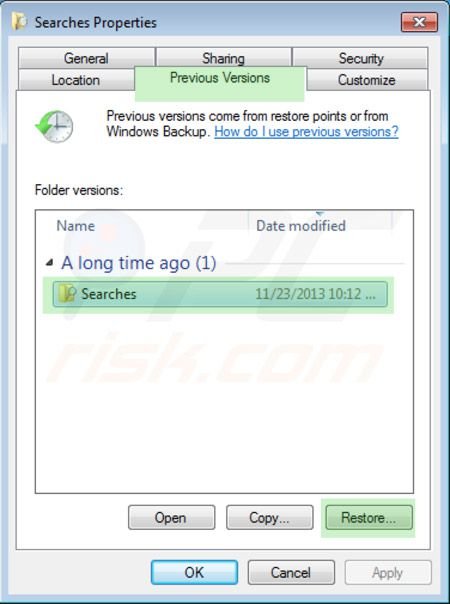
To restore individual files encrypted by this ransomware, try using Windows Previous Versions feature. This method is only effective if the System Restore function was enabled on an infected operating system. Note that some variants of LLTP are known to remove Shadow Volume Copies of the files, so this method may not work on all computers.
To restore a file, right-click over it, go into Properties, and select the Previous Versions tab. If the relevant file has a Restore Point, select it and click the "Restore" button.
If you cannot start your computer in Safe Mode with Networking (or with Command Prompt), boot your computer using a rescue disk. Some variants of ransomware disable Safe Mode making its removal complicated. For this step, you require access to another computer.
To regain control of the files encrypted by LLTP, you can also try using a program called Shadow Explorer. More information on how to use this program is available here.
To protect your computer from file encryption ransomware such as this, use reputable antivirus and anti-spyware programs. As an extra protection method, you can use programs called HitmanPro.Alert and EasySync CryptoMonitor, which artificially implant group policy objects into the registry to block rogue programs such as LLTP ransomware.
HitmanPro.Alert CryptoGuard - detects encryption of files and neutralises any attempts without need for user-intervention:
Malwarebytes Anti-Ransomware Beta uses advanced proactive technology that monitors ransomware activity and terminates it immediately - before reaching users' files:
- The best way to avoid damage from ransomware infections is to maintain regular up-to-date backups. More information on online backup solutions and data recovery software Here.
Comments
Post a Comment